Single Sign On Guide: Secure Login Solutions
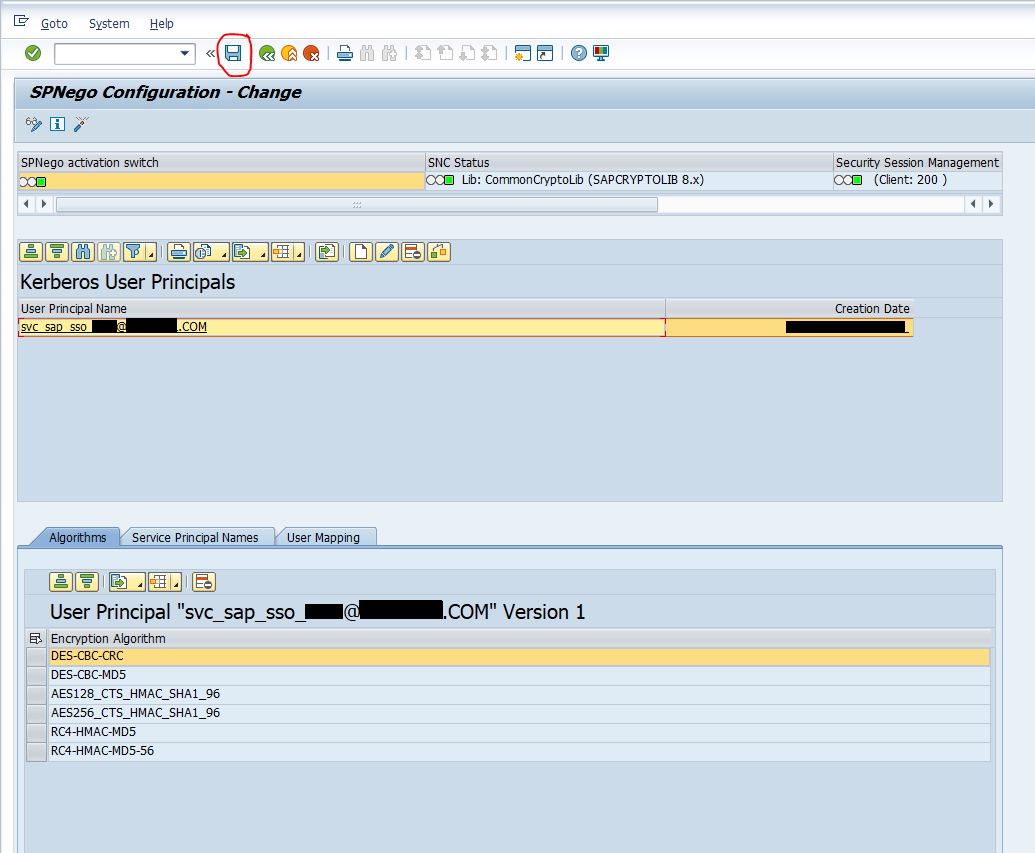
The concept of Single Sign-On (SSO) has become a crucial aspect of modern authentication systems, providing users with a seamless and secure login experience across multiple applications and services. In this comprehensive guide, we will delve into the world of SSO, exploring its benefits, types, and implementation strategies, as well as discussing the latest trends and best practices in the industry.
Introduction to Single Sign-On
Single Sign-On is an authentication process that allows users to access multiple applications, systems, or services with a single set of login credentials. This approach eliminates the need for users to remember multiple usernames and passwords, reducing the risk of password fatigue and improving overall productivity. SSO solutions are widely used in various industries, including finance, healthcare, education, and government, where secure access to sensitive information is paramount.
Benefits of Single Sign-On
The benefits of implementing SSO solutions are numerous. Some of the most significant advantages include:
- Improved user experience: SSO provides users with a seamless and convenient login experience, reducing the time and effort required to access multiple applications.
- Enhanced security: By reducing the number of login credentials, SSO solutions minimize the risk of password-related security breaches and phishing attacks.
- Increased productivity: With SSO, users can quickly and easily access the resources they need, without being hindered by multiple login prompts.
- Reduced helpdesk costs: By eliminating the need for users to remember multiple passwords, SSO solutions reduce the number of password-related support requests, resulting in lower helpdesk costs.
Types of Single Sign-On Solutions

There are several types of SSO solutions available, each with its own strengths and weaknesses. Some of the most common types include:
1. Kerberos-based SSO: This type of SSO uses the Kerberos protocol to authenticate users and provide access to applications and services. Kerberos-based SSO is widely used in Windows-based environments and is known for its high level of security and scalability.
2. Form-based SSO: This type of SSO uses a web-based form to collect user credentials and authenticate access to applications and services. Form-based SSO is commonly used in web-based applications and is known for its ease of implementation and flexibility.
3. Smart Card-based SSO: This type of SSO uses smart cards or other forms of two-factor authentication to provide secure access to applications and services. Smart Card-based SSO is widely used in high-security environments, such as government and finance, where strong authentication is required.
Implementation Strategies
Implementing an SSO solution requires careful planning and execution. Some of the key strategies to consider include:
1. Assessing business requirements: Before implementing an SSO solution, it’s essential to assess business requirements and identify the applications and services that need to be integrated.
2. Choosing an SSO protocol: Selecting the right SSO protocol is critical to ensuring the security and scalability of the solution. Common SSO protocols include SAML, OAuth, and OpenID Connect.
3. Configuring SSO settings: Configuring SSO settings, such as authentication modes and session timeouts, is essential to ensuring the secure and seamless operation of the solution.
| SSO Protocol | Description |
|---|---|
| SAML (Security Assertion Markup Language) | An XML-based protocol used for exchanging authentication and authorization data between applications and services. |
| OAuth (Open Authorization) | A protocol used for delegated authorization, allowing users to grant applications limited access to their resources without sharing passwords. |
| OpenID Connect | An identity layer built on top of the OAuth protocol, providing a standardized way for applications to authenticate users and obtain their identity information. |

Best Practices for Implementing SSO Solutions
Implementing an SSO solution requires careful planning and execution. Some of the best practices to consider include:
1. Conducting a thorough risk assessment: Before implementing an SSO solution, it’s essential to conduct a thorough risk assessment to identify potential security vulnerabilities and mitigate them.
2. Choosing a scalable SSO solution: Selecting an SSO solution that can scale to meet the needs of the organization is critical to ensuring the solution remains effective and efficient over time.
3. Providing user training and support: Providing user training and support is essential to ensuring a smooth transition to the SSO solution and minimizing the risk of user errors and security breaches.
Future Implications of SSO Solutions
The future of SSO solutions looks promising, with emerging trends and technologies, such as artificial intelligence and machine learning, expected to play a major role in shaping the industry. Some of the key future implications of SSO solutions include:
1. Increased adoption of cloud-based SSO solutions: Cloud-based SSO solutions are expected to become increasingly popular, offering organizations greater flexibility and scalability.
2. Growing use of biometric authentication: Biometric authentication, such as facial recognition and fingerprint scanning, is expected to become more widespread, providing users with a more secure and convenient login experience.
3. Greater emphasis on identity and access management: As organizations increasingly adopt SSO solutions, there will be a growing need for robust identity and access management strategies to ensure the security and integrity of user identities.
What is Single Sign-On (SSO)?
+Single Sign-On (SSO) is an authentication process that allows users to access multiple applications, systems, or services with a single set of login credentials.
What are the benefits of implementing an SSO solution?
+The benefits of implementing an SSO solution include improved user experience, enhanced security, increased productivity, and reduced helpdesk costs.
What types of SSO solutions are available?
+There are several types of SSO solutions available, including Kerberos-based SSO, form-based SSO, and smart card-based SSO.
How do I implement an SSO solution?
+To implement an SSO solution, you should assess your business requirements, choose an SSO protocol, configure SSO settings, and provide user training and support.
What are the future implications of SSO solutions?
+The future implications of SSO solutions include increased adoption of cloud-based SSO solutions, growing use of biometric authentication, and greater emphasis on identity and access management.



